What is it?
This website offers a NTLM to plaintext password "cracking" service, using a custom high performance database with billions of precomputed password hashes. It by no means cover anything near the possible combinations, but will probably give you way more results than it should on a regular Active Directory dump.
The services are meant to be used by curious learners doing labs, security professionals doing authorized security audits for companies, or people participating in CTFs. Expect your lookup rate here to be anywhere between 5-25% if you use this with an average Active Directory deployment, while a day long Hashcat cracking cycle on a single GPU system will probably give you between 40-60% results (based on my own experience).
Should I even use this?
You MUST read the section about unintended consequences before using this site with real world hashes!
Terms of use
Services provided on ntlm.pw are offered without warranties, either expressed or implied. Users acknowledge and accept that all services are rendered as-is, without any guarantee of performance or suitability for specific purposes. ntlm.pw disclaims any implied warranties, including but not limited to merchantability or fitness for a particular purpose.
Users utilize the services at their own risk, and ntlm.pw or its operators holds no liability for any consequences arising from their use of the services.
F.A.Q.
"Can I have a copy of the database?"
No. I strongly believe in sharing things with the infosec community, and I have lots of free stuff including source code for multiple projects on GitHub. However this project is different, and I will not be openly publishing the source code or the dataset it contains.
The initial database is a collection of leaked passwords from various sources, and various pattern generated passwords. There is not enough additional magic that will bring value by sharing the list. You can compile most of the list yourself, just poke around and find it.
I want to be able to grow the dataset without compromising any users of the site, and sharing collected data with others would undermine that. Yes, you can ask for the hash for BigCompany2024 and I might have it, but I will not tell you if it's because a user has submitted a hash or if I myself have added it.
"I will not share my super sekrit hashes with some rando"
This is understandable, and very much your choice.
"You're enabling hackers"
There are two sides to all investigative security tools - they can be used for either good or bad. But if your organizations safety is based on hackers not being able to figure out how to crack a password, you'll be in for a rude awakening if they ever get inside your company.
How to secure your Active Directory
Passwords are important, but more important is becoming aware of and remediating typical attack scenarios seen in most corporate environments. Pentesters and ransomware threat actors have a field day with compromising companies, simply because they aim too high with security projects and forget about the low hanging fruits that will make all other efforts worthless.
Active Directory Tools
Adalanche
I've spent three years making my open source project Adalanche to lower the bar for system administrators to find and fix low hanging fruits.
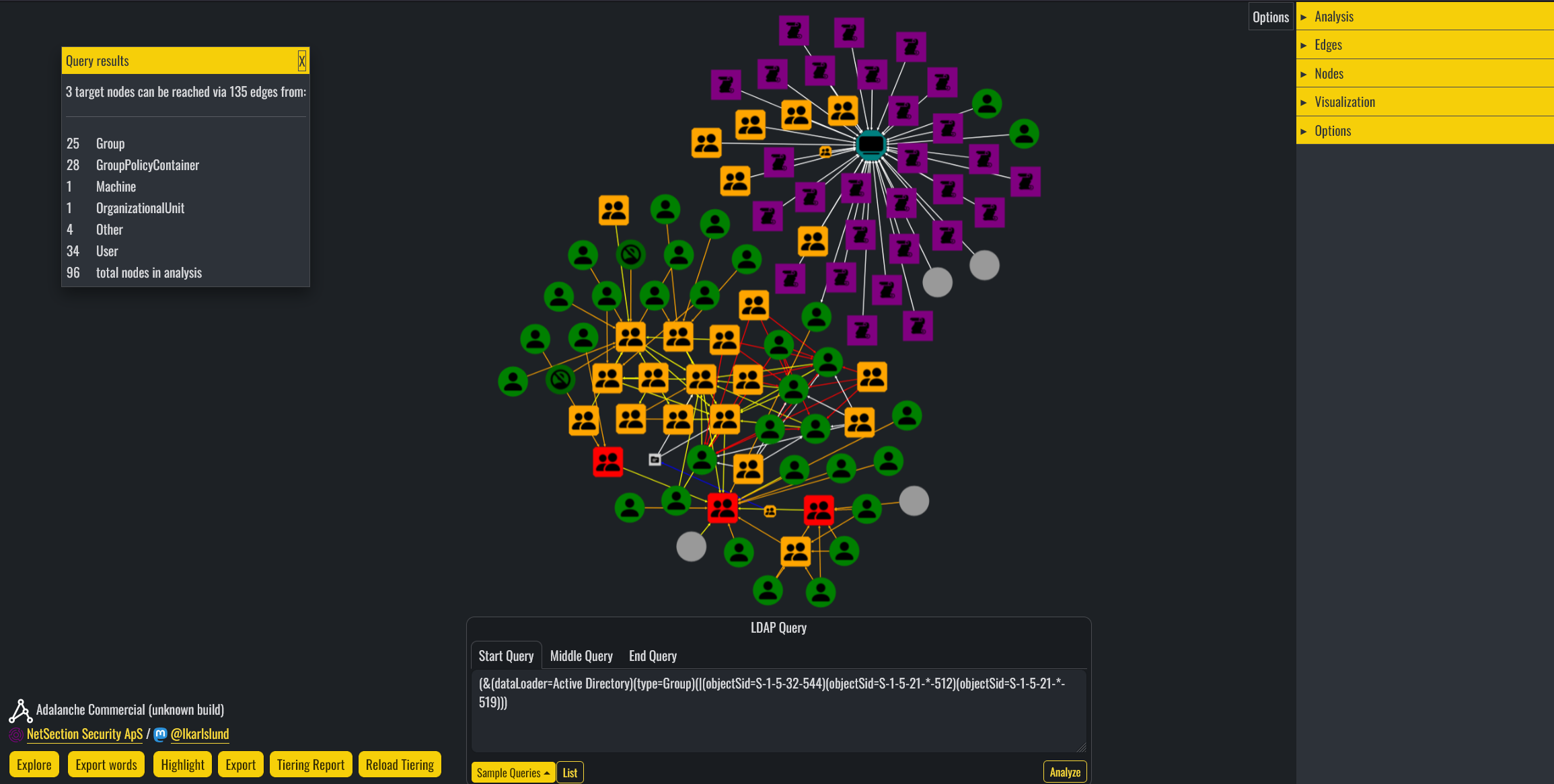
It helps you search for and explore the attack graphs that influence the way hackers will navigate through your Active Directory. It's free, and if you haven't run something on your Active Directory, I'm sure you will get results. Go fix!
There's a paid version as well, that does more advanced analytics and integrates with VMware vCenter, CyberArk, can ingest hashes and show you password reuse across accounts etc. There's information about that on NetSection.
LDAP Nom Nom
For pentesters or just the curious sysadmin, you can find usernames from any Domain Controller without credentials and it doesn't get noticed or logged.
You can grab LDAP Nom Nom and see what falls out of your AD. If you have any accounts where the username and the password is the same, it's fairly certain that in case your organization ever gets hacked this will be abused.
Like or dislike ntlm.pw?
... and have comments or input - feel free to get in contact on Mastodon @lkarlslund, Twitter @lkarlslund, or LinkedIn Lars Karlslund.Shoutouts
The Hashcat crew, hashmob.net, HIBP, mRr3b00t and everone else that makes the world a little more secure!
Database has 8.726.485.619 unique hashes. Quota 10000 points, resets in 900 seconds.
Took 0.15ms
